Virus and Spyware Removal Guides, uninstall instructions
What kind of application is ProjectRootEducate?
While inspecting new file submissions to the VirusTotal site, our research team discovered the ProjectRootEducate app. After analyzing it, we learned that this application is adware from the AdLoad malware family. ProjectRootEducate is designed to generate revenue for its developers through advertising.
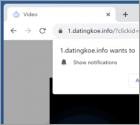
What kind of page is datingkoe[.]info?
While investigating suspicious websites, our researchers discovered the datingkoe[.]info rogue webpage. It operates by promoting browser notification spam and redirecting users to other (likely untrustworthy/dangerous) sites.
Most visitors to datingkoe[.]info and pages akin to it access them through redirects generated by websites that employ rogue advertising networks.
What kind of application is OpenProcess?
OpenProcess is a piece of software that is classified as adware. Our researchers found this application during a routine investigation of new file submissions to the VirusTotal platform. OpenProcess belongs to the AdLoad malware family, and it runs intrusive advertisement campaigns.
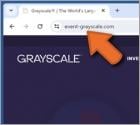
What is the fake "Grayscale ($GRAY) Airdrop"?
After investigating the "Grayscale ($GRAY) Airdrop", as promoted on event-grayscale[.]com, we determined that it is fake. This scam is an almost perfect copy of the Grayscale platform (grayscale.com).
This bogus giveaway operates as a crypto drainer that siphons cryptocurrency from compromised digital wallets. It must be stressed that this scheme is not associated with any existing platforms or entities.
What kind of application is PublicAnalog?
During our analysis of PublicAnalog we observed that the app functions as adware. While active, it delivers annoying advertisements. It is also common for apps like PublicAnalog to be capable of accessing (and gathering) various data. Thus, it is recommended to uninstall PublicAnalog from affected devices.
What kind of malware is WaveStealer?
WaveStealer (also known as Wave Stealer) is a malware designed to steal information. Its developers are offering the malicious program for sale, and they promote it as a highly versatile tool. WaveStealer targets log-in credentials (usernames/passwords), credit card numbers, cryptocurrency wallets, and other sensitive data.

What kind of website is brandnewsearch.com?
Brandnewsearch.com is the address of a fake search engine. It is endorsed (via redirects) by the Brand New Search rogue browser extension. It modifies browser settings to generate these redirects, and due to this behavior – Brand New Search is categorized as a browser hijacker.

What kind of malware is Wpeeper?
Wpeeper is the name of a backdoor malware targeting Android users. This piece of malware is capable of stealing various data, downloading files, deleting itself from infected devices, and more. Android users should be cautious and take steps to protect their devices from such threats. If Wpeeper is already present on a device, it should be removed immediately.
What is the fake "Renzo ($REZ) Token Allocation" website?
We have inspected claim-renzoprotocol[.]network site and found that it is a deceptive website promoting a Renzo ($REZ) Token Allocation. This scam website mimics the real Renzo site (renzoprotocol.com) and is designed to steal cryptocurrency. Thus, individuals should be careful when encountering fake promotions like Renzo ($REZ) Token Allocation.

What kind of malware is KUZA?
Our research team discovered KUZA ransomware while investigating file submissions to the VirusTotal website. This malicious program is a variant of the Proton ransomware.
On our testing machine, KUZA encrypted files and altered their filenames. Original titles were appended with the attackers' email address and a ".Ripa" extension. For example, a file initially named "1.jpg" appeared as "1.jpg.[amir206amiri2065sa@gmail.com].Ripa".
After the encryption process was finished, this ransomware changed the desktop wallpaper and dropped a ransom-demanding message with "#Read-for-recovery.txt" as the filename.
More Articles...
Page 1 of 2139
<< Start < Prev 1 2 3 4 5 6 7 8 9 10 Next > End >>