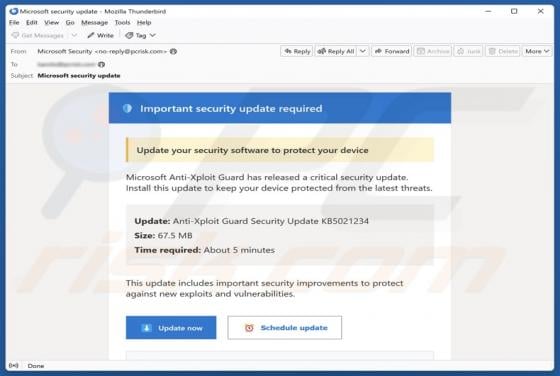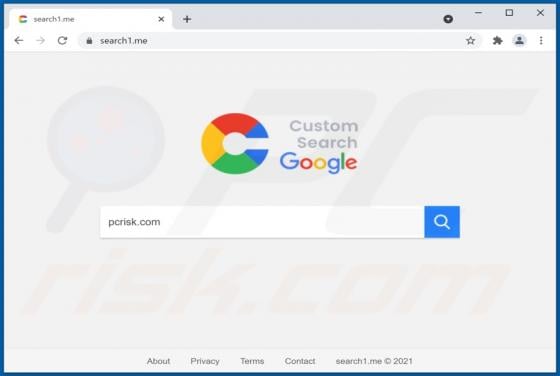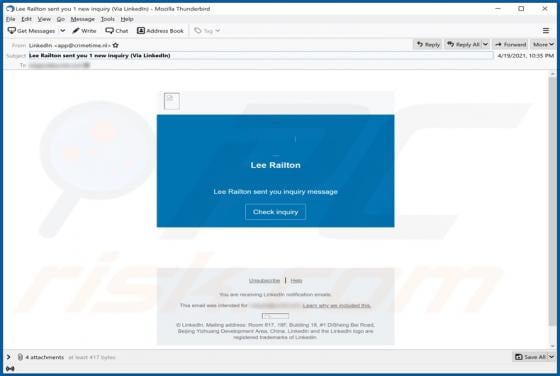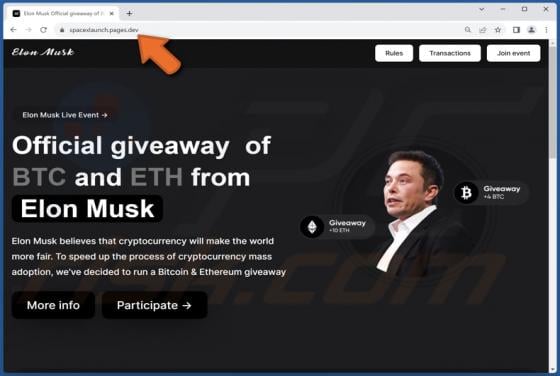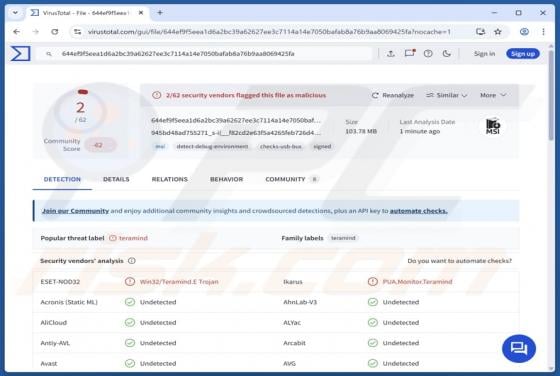
Trojanized Teramind Software
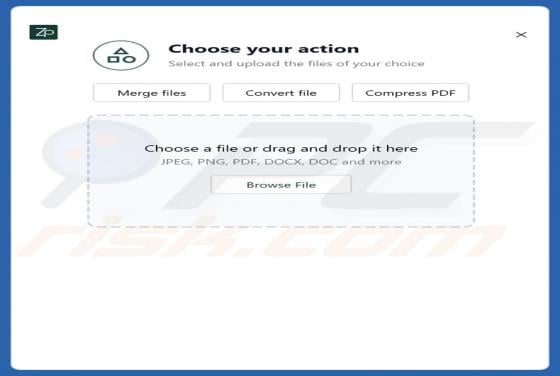
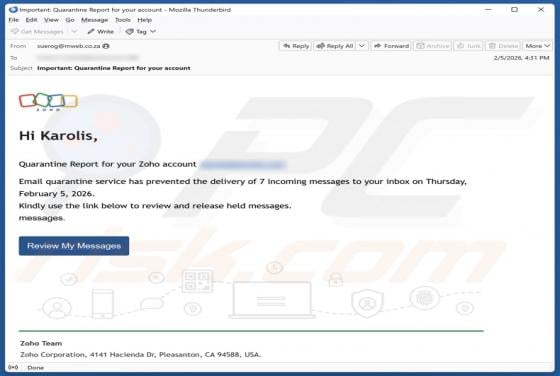
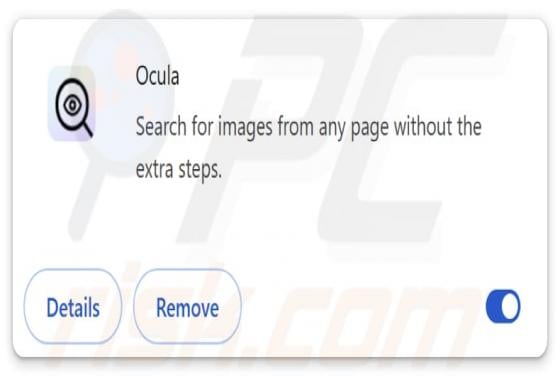
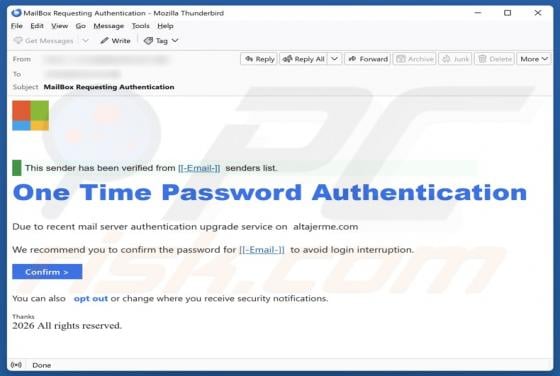
This article describes how cybercriminals abuse a legitimate remote administration tool called Teramind for malicious purposes. Remote access tools allow users to control or access a device from another location over the internet. When used by cybercriminals, they can secretly access a victim's de